Upon a review of support notes from Oracle Metalink, the following notes will come in useful for our in depth analysis and review of how to manage SSL with Oracle 10gAS:
Note: 351341.1 - How To Setup and Configure SSO/OHS for SSL
Note 351340.1 - How To Create SSL Wallet Using Wallet Manager and Oracle Certificate Authority
Note 351365.1 - How To Set up and Configure SSO and OIDDAS to use SSL
I highly recommend that all Oracle DBAs and analysts read and digest these Metalink support notes before you configure SSL for Oracle 10g Application Server so that problems are avoided and success ensured for your SSL administration tasks. By doing so, you will prevent many headaches and avoid potential gotchas. I usually make a point to read the release notes and Metalink notes before I perform a major task for a new environment as it saves me hours of frustration. Since we are using a demo lab based environment, some of these tasks from Metalink will not apply but the key concepts still are valid. Now lets move on from where we left off last time which is to configure the Oracle Wallet Manager (OWM) environment so that we can setup a new set of wallets for our certificates for use with SSL and Oracle 10g Application Server.
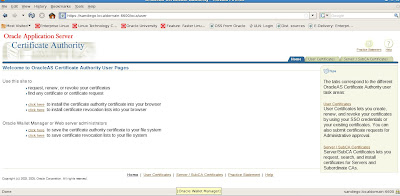
Now that we have setup our Oracle Certificate Authority (OCA) to use trusted certificates for SSL connections, we can proceed to configure new wallets with Oracle Wallet Manager (OWM) for Oracle 10g Application Server. In contrast to the OCA administration pages located under https://server:
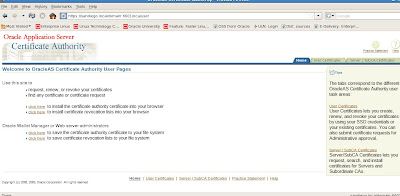
This differs from the OCA administrator site that provides maintenance options for certificate management with the Oracle certificate authority (OCA) in that user certificates can be viewed and managed on the user site.

From the user menu sitre we can trust and view the certificates to be authenticated by Oracle 10g Application server.
We can also import the Certificate Revoke Lists (CRL) that we saw earlier.

Now lets try to see if our previous certificate is accepted when we attempt to connect to SSO and OCA via SSL.
We click on the right tab option for User Certificates
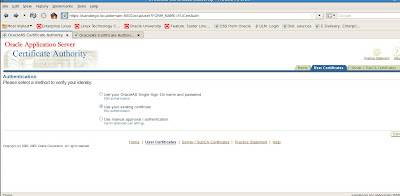
We try the option by using our existing certificate
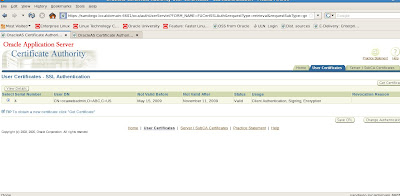
OK, so we have several things that we can do from this screen. We can examine the certificate in further detail as well as update the CRL (Certificate Revocation list), get the certificate, as well as change authentication options.
If we choose to get our certificate we can update options for managing our certificate. Now, we need to configure our server side certificate options. For this task, we need to use the Oracle Wallet Manager (OWM)
Oracle Wallet Manager (OWM)
So at this point you are probably wondering, what exactly does this Oracle Wallet Manager (OWM) do and why do I need it? Well, the Oracle Wallet Manager (OWM) is an integral component of SSL authentication. As such, it performs the following key tasks for Identity Management with Oracle 10g Application Server for SSL:
- generates public/private key pair
- creates certificate request
- installs certificates
- configures trusted certificates
- creates the wallet which is accessed by the Oracle Wallet Manager (OWM)
- uploads contents of wallet to LDAP directory systems such as Oracle Internet Directory (OID)
- imports and exports wallets
The Oracle Wallet Manager tool (OWM) is located under $ORACLE_HOME/bin directory for the Oracle 10gAS Infrastructure environment. New wallets must use a password based on the following standard of minimum 8 characters with at least one alphabetic and numeric or special character. The OWM users trusted and user based certificates. One caveat is that you need to install a trusted certificate first before using a user certificate issued by the certificate authority (CA). Wallets can be exported and imported as well. We also will need to configure our end user web browser to trust the OCA. This varies based on your browser version and configuration. We will provide an example of this shortly.
We also need to enable the Oracle HTTP (Apache 1.3) server (OHS) to use SSL. This will be discussed in the third installment for SSL and Oracle 10gAS. Finally, we need to use the SSL configuration tool to automate changes for securing HTTP. Furthernmore, we need to add user certificates to the Oracle Internet Directory (OID) via the ldapmodify command or via an ldif file.
Since we are using a single web browser for our lab environment and Mozilla Firefox in this case, we need to clear out old certificates before we configure a new wallet for Oracle 10g Application Server. We also need to enable Mozilla Firefox to accept certificates. Under our browser window we need to EDIT->PREFERENCES which brings up the options for certificates.
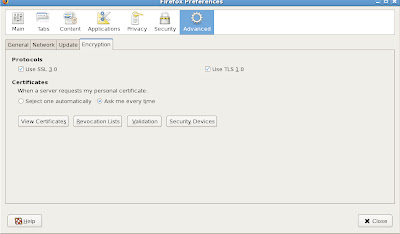
Make sure to select the option for "Ask Every Time" otherwise errors may occur for our certificate authentication processing.
We also need to clean out old OCA web administrator certificates from previous tasks. To do this, we need to stop and restart our OCA server. We can use the $ORACLE_HOME/oca/bin/ocactl stop then $ORACLE_HOME/oca/bin/ocactl revokecert and then restart OCA server with the $ORACLE_HOME/oca/bin/ocactl start command as shown in the following example.
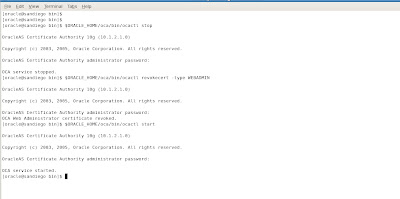
Now we are all set and ready to create a new wallet! To start the Oracle Wallet Manager (OWM) we simply open another terminal shell command window and execute the owm from $ORACLE_HOME/bin directory
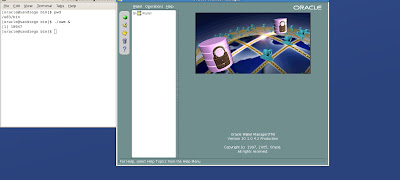
From the main OWM screen, we can perform many tasks such as creating new wallets, importing or exporting wallets just to name a few tasks. Now let's create a new wallet.
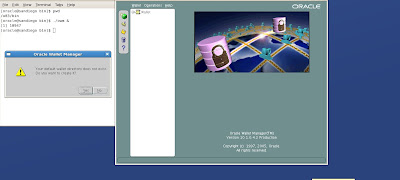
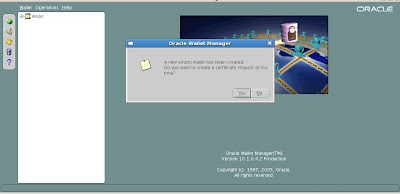
Oracle Wallet Manager (OWM) asks us if we wish to create a new default wallet. We choose Yes and it complains that it cannot create a default wallet in the system directory with message of "Unable to create system default wallet directory."
We continue anyways and ignore the error warning message

Now we need to enter a wallet password and choose authentication option
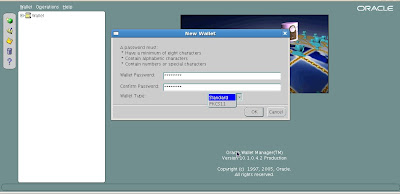
We have a choice between standard wallet type of PKCS11 wallet type that we discussed earlier. Lets keep with standard wallet type for sake of simplicity.
Our wallet is created successfully and OWM asks us if we would like to create a new certificate request to link to the new wallet. Since we need to do this, we enter the following details for our new certificate request. We choose to keep the default key size to 1024 bits.
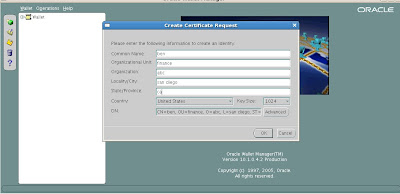
We confirm our choices for the new certificate request and click the OK button.
Now we can see that the new certificate request has been successfully created by OWM.
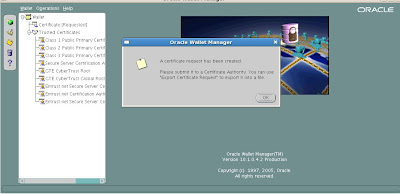
We still need to submit the certificate for acceptance to the OCA via the user pages that we saw earlier.
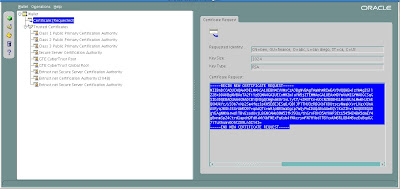
To view and obtain the details for our new certificate created by OWM we can examine the details under the menu tree for Wallet-> Certificate [Requested] as shown in the figure example below:
What we need to do is to clear entries from the web browser so that old certificates do not appear since we want to login to the OCA as a user and not as an administrator.
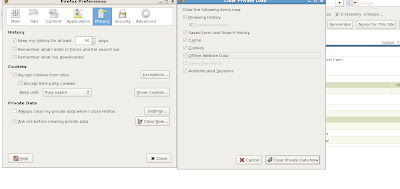
Also be sure to delete old certificates to avoid problems since in our test environment we have a single web browser and server used. Now we need to return back to our OWM window that had the certificate details from our newly created certificate request. Open a new browser window in tandem with having OWM open and connect to the Oracle Certificate Authority User page via SSL based on https://host_name.
In our case, we connect to SSL port 6600
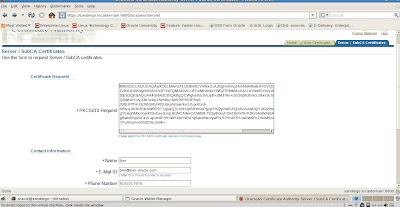
Now we need to copy the certificate details from our new certificate request from OWM from BEGIN NEW CERTIFICATE REQUEST until END NEW CERTIFICATE REQUEST
Move back to the User OCA page and click on Request a new certificate on the Server/SubCA Certificates tab
Now we need to choose the option "Request A Certificate"
Paste the new certificate request encrypted details from OWM into the main field as shown below
Enter personal information in the fields and click OK to submit the request to the OCA.
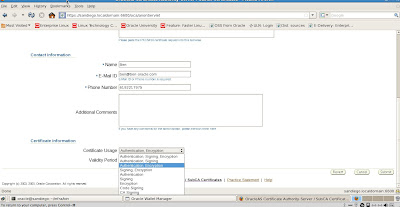
Now we need to generate the server certificate. Click the Submit button. We verify that it is accepted by the OCA
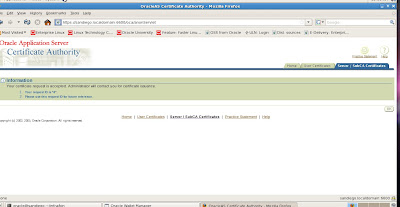
Our certificate request has been accepted and stored in the OID server. Now we can exit OWM and need to approve the new certificate request from the OCA Administration page. We can cancel saving the new wallet as that is not required. Now lets take a look at how to approve the new certificate request.
Since we are doing this on same server and web browser we need to shutdown the OCA server, revoke old admin certificates, remove them from our browser and restart the OCA services.

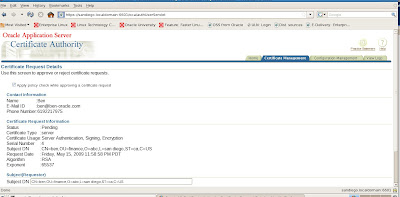
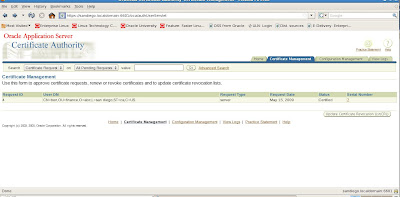
We now see the new certificate details for review to either approve or reject the requests
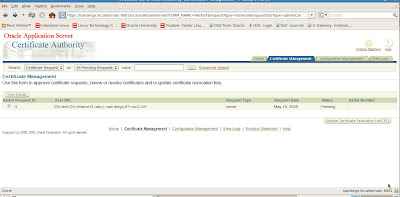
Lets go ahead and approve the new certificate request by View Details
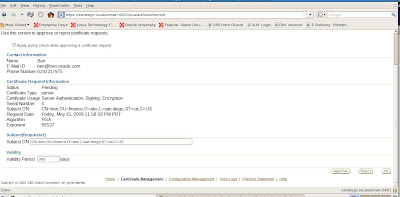
When we submit approval the OCA prompts us once more to make sure we wish to approve the new certificate request
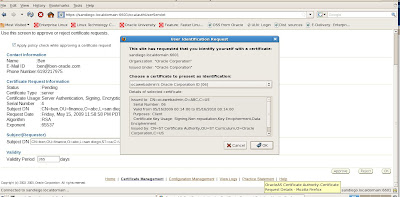
Our new certificate request is approved status and shown below

Now we can verify that the newly created certificate request is available with OCA
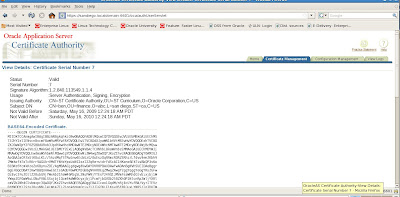
We can also verify the encoded certificate details given in BASE64 format:
We will continue our setup for SSL with Oracle 10g Application server in the next installment as the final steps require us to modify configuration to the OHS (Oracle HTTP Server aka Apache 1.3).










No comments:
Post a Comment