Our series continues for Oracle Fusion Middleware technology with a focus on Oracle Application Server (10gAS). The following will be topics for Fusion Middleware:
Part I: Identity Management- OID and SSO
Part II: Tips and Tricks for Monitoring and Troubleshooting Oracle Application Server
Part III: Performance Tuning Oracle Application Server
As part of our new Fusion Middleware series of tips for Oracle database technology, this week will cover
how to configure the complex identity management piece (IdM) for Oracle 10gR2 Application Server (OAS)
by using the Oracle Internet Directory (OID) component of the Oracle 10g Application Server infrastructure.
What is the Oracle Application Server (OAS) ? The Oracle 10gAS is a robust technology that provides a multitude of web server
and rich content management functions for customer applications. It is the heart of many core Oracle enterprise technologies such as Oracle EBS and additional technologies that require web inter/intranet functionality.
For our case study, we will use a full blown installation of Oracle 10gR2 Application Server (10.1.2.0.2) on the Oracle Enterprise 5 Linux 32 bit platform (OEL 5.3) . Since Fusion Middleware is a suite of 200+ products, we will only cover Application Server for the time being in our Fusion Middleware series before we move onto other core topics such as BPEL and SOA (Service Oriented Architecture). What are the components of the Oracle 10g Application Server? There are two major pieces: the middle tier application server and the second technical stack is called the Infrastructure. In a standard OAS installation, one only needs to use the middle tier application server for most purposes. The infrastructure is an optional enterprise tech stack that is not always required. In essence, we have an n-tiered architecture that makes up the structure for an Oracle 10gAS environment: web tier, middle tier, and infrastructure. First, lets review the components of the middle tier for Oracle 10g Application server.
Web Tier
- Oracle HTTP Server (OHS) which is the Oracle modified version of the Apache HTTP server with a few twists unique to Oracle
- Oracle Application Server Web Cache (optional): provides enhancement in performance for caching web page content
and some software based load balancing features
Middle Tier Oracle 10g Application Server (10.1.2 OracleAS)
- OC4J server which is the Oracle Container for Java Enterprise Edition and the heart of the Oracle 10g Application Server
- Oracle Portal: rich web based content management system for portlets and web applications
- Oracle Wireless: for handheld wireless devices to access web rich database applications
Infrastructure Components of OracleAS 10gR2:
The infrastructure architecture of Oracle 10g Application Server consists of two core technical items:
Identity Management: includes Oracle Internet Directory(OID), Single Sign On (SSO)
Metadata Repository which is an Oracle 10g database which stores metadata for OAS application services such as OID and
SSL.
Oracle recommends at least a 2-3 tiered approach to optimize performance and provide for optional load balancing solution.
One key area within the Oracle Application Server that is poorly understood is Identity Management. Identity management provides many security administration functions to streamline access to Oracle web systems such as Single Sign On (SSO) authentication. Single Sign On allows a user to access multiple Oracle web applications with a single user name and password that is authenticated against the OAS and Oracle database environments. Stay tuned as we will cover SSO in future installments. For now, hang on and we will return to OID and Application Server setup. The reason why I chose to cover OID first is that now Oracle 10gAS requires a full setup with OID before installation of Discoverer for the Business Intelligence (BI) environment. What is OID? OID or Oracle Internet Directory is the Oracle LDAP implementation (Lightweight Directory Access Protocol) with Application Server. I like to think of OID is Microsoft Active Directory on steroids for Oracle. So for those of you who are new to LDAP, to break it down in simple terms. LDAP has a name structure based on an inverted tree as shown below:

Suffice it to say, a discussion of LDAP is beyond scope of our discussion for Oracle 10gAS but a good reference on LDAP is available in the Oracle Internet Directory Administrator's Guide 10g available at .
OK, lets get started with configuration for Oracle Internet Directory (OID) with Oracle 10g Application Server. One useful item to mention is the help system that comes with OAS as shown in the below figure example:
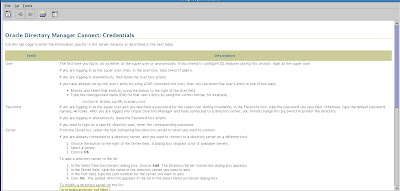
Now, lets start a new session to configure OID. Of note: OID can also be configured for non-Application Server environments. For instance, we can setup OID with Oracle 11g. The OID security is available from the Network Configuration Assistant (netca) to setup the Oracle Internet Directory with Oracle database environments. For Oracle 10gAS, the method to setup and configure OID is to use the oidadmin utility.
Back to our Oracle 10gAS environment. The oidadmin utility is located under our $ORACLE_HOME/bin directory. Make sure to correctly set your Oracle environment variables for your operating system. We start oidadmin and the welcome screen appears below.
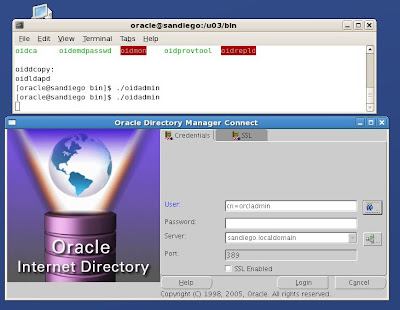
We need to login to OID as the default administrator. Since OID uses LDAP, we need to specify the login format based on common name (CN)
cn=orcladmin
password= the password for ias_admin account that we chose during the Oracle 10gAS installation process.
Then we login. The welcome screen appears and shows our default OID environment.
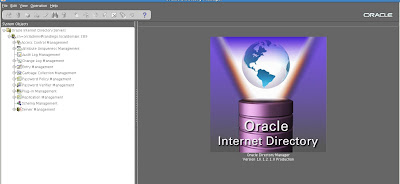
Now, let's expand the tree structures to expose the various configuration details for OID with our 10gAS environment.
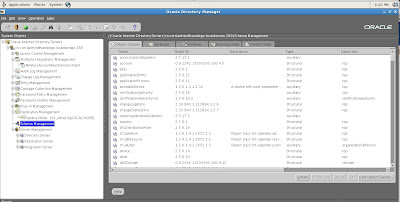
As you can see, multiple tasks can be performed to administer users and servers within the OID environment for Oracle 10gAS.
Suffice it to say, it would require an entire book to detail all aspects of Oracle Identity management with Oracle 10g Application Server. For now, we will provide a basic walkthrough to get the baseline configuration up and running with our new 10g Application Server. There are three divisions of OID configuration to consider:
1. Access Control Management
2. Schema Management
3. Server Management
Access Control Management
First we will consider Access Control Management with OID. Access Control management is the process of granting and restricting access to a realm of Oracle application or database servers within the Oracle Internet Directory (OID) environment for Identity Management.
Access controls can be managed and created via the OID interface for applications and users based on the OID LDAP X.509 standard using cn (common name) and LDAP syntax. For example, we have the cn=Reports details displayed for Access Control Management listed below.
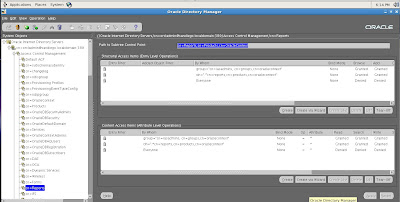
Schema Management for OID and Identity Management
By default, OID stores all metadata about configuration details and users in a set of schemas within the Oracle 10g repository database which is part of the Infrastructure component of Oracle 10gAS.
Each schema item is broken down into subitems such as object id, class, and attributes based on the LDAP syntax for OID as shown below.
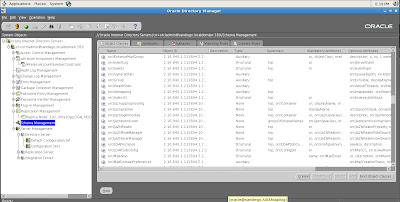
Now let's move on to showcase server management for OID and 10g Application Server.
Server Management for OID and Identity Management
OID provides various types of server configurations for Oracle 10gAS:
- Directory Server
- Replication Server
- Integration Server
These servers determine the specific type of security mechanism and configuration to be used with Oracle 10g Application Server. For example, to view, change and update settings for our directory server we would expand the tree structure menu item under Server management:
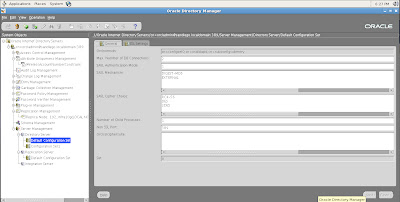
We also have options to modify settings for SSL (Secure Sockets Layer):
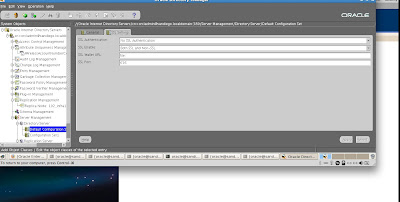
Now let's move on to configuration tasks for Oracle 10g Application Server with a basic Identity Management setup. So, we return to our Oracle 10gAS control window.
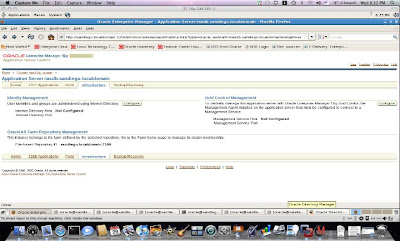
To access the settings for Identity Management, we navigate to the Infrastructure tab on our Application Server Enterprise Manager. As expected, it shows us that nothing has been configured yet. We click on the configure tab.
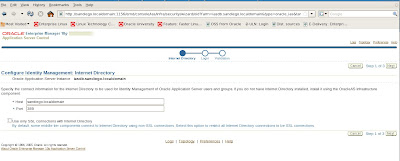
We enter the hostname details for our 10g Application Server, port number.
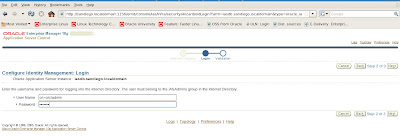
Recall that we need to specify the username in LDAP format with cn=orcladmin and the password for ias_admin that
was given during the Oracle 10gAS installation. Oracle then politely informs us that the entire tech stack for Oracle 10g Application Server will be shutdown and restarted to complete our basic Identity Management configuration. We verify all settings are correct.
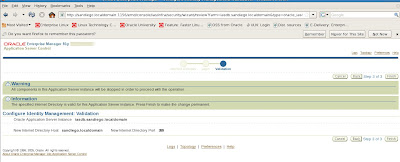
Now our configuration setup should be complete for a baseline Identity Management install. Our next post will detail basic SSO configuration for Oracle 10g Application Server.
Cheers,
Ben










No comments:
Post a Comment